Perimeter Protection Icon
Perimeter security icons Clipart Fotosearch Enhanced k Fotosearch Stock Photography and Stock Footage helps you find the perfect photo or footage, fast!.

Perimeter protection icon. Designing a perimeter intrusion detection system (PIDS) requires skill Inclement weather, adverse lighting, limited power, and challenging environments are factors system integrators must mitigate by choosing the right technologies While requiring more upfront technical design, endtoend solutions are highly effective in advancing a customer’s overall perimeter security and crime. The best selection of Royalty Free Perimeter Vector Art, Graphics and Stock Illustrations Download 1,0 Royalty Free Perimeter Vector Images. Perimeter Security Manager II (PSM II) is an advanced, Windows®based security monitoring and control application that provides powerful intrusion detection system management capabilities and ease of use The system is ideal for users seeking to manage numerous perimeter security devices and visual assessment tools across single or multiple networked locations PSM II monitors, displays and.
Lined perimeter security icon set by S Leonov premium vector (SVG) icons in Computer & internet security · Added on Oct 31st, 19 Add to cart $2400 Premium icon set Basic license Icon sets from the Lined Icons icon family 2,215 icons in 111 icon sets Lined snowboarding. ©21 Perimeter Protection Products, LLC custom responsive website designed by JAM graphics. Perimeter security consists of integrated elements and systems, both electronic and mechanical, that protect a physical area such as a company or an airport that dissuade and detect intruders The main perimeter security challenges are reliability of detection, the behaviour of devices in adverse weather conditions, suitability for the physical characteristics of the perimeter.
TRICON Construction is a diversified company focusing primarily on perimeter security installations In state or out of state we know what it takes to get your project done safely and efficiently Our capabilities also include concrete, excavation, underground utility and septic work. Outline Perimeter Security Icons Simple set of perimeter security related vector icons for your design Note This purchase is a single image file Image Editor Save Comp Similar Illustrations See All Traces on the ground, service shepherd, security camera, fingerprint Prison set collection icons in outline style vector symbol stock. IP67 and IK09 rated, allweather approved.
Physical security controls include such things as data center perimeter fencing, locks, guards, access control cards, biometric access control systems, surveillance cameras, and intrusion detection sensors Digital security controls include such things as usernames and passwords, twofactor authentication, antivirus software, and firewalls. Whistler XTR140 Radar/Laser Detector, Icon display, Exclusive LED alert periscope, 360º Total Perimeter Protection, 3 city modes/highway mode, Highgain lens, Tone alerts, Quiet/auto quiet modes, Alert priority, Vehicle battery saver, Patented VG2 Cloaking Technology (XTR 140 XTR140). Perimeter Security Manager II (PSM II) is an advanced, Windows®based security monitoring and control application that provides powerful intrusion detection system management capabilities and ease of use The system is ideal for users seeking to manage numerous perimeter security devices and visual assessment tools across single or multiple networked locations PSM II monitors, displays and.
TRICON Construction is a diversified company focusing primarily on perimeter security installations In state or out of state we know what it takes to get your project done safely and efficiently Our capabilities also include concrete, excavation, underground utility and septic work. A sound network security perimeter architecture requires multiple layers of defense, uptodate and hardened policies and controls and segmentation All of these things make it harder for an attacker to gain access to your crown jewels and easier for you to isolate and respond to breaches when they occur. Lined perimeter security icon set by S Leonov premium vector (SVG) icons in Computer & internet security · Added on Oct 31st, 19 Add to cart $2400 Premium icon set Basic license Icon sets from the Lined Icons icon family 2,215 icons in 111 icon sets Lined snowboarding.
Perimeter Protection Best Practices 1 Deter The best thing you can do to an intruder, or should I say a potential intruder, is to deter them from even thinking of further penetration into the facility This can start with simple measures such as the presence of warning signs, audio announcements, lighting, guard dogs, robots and fences topped. Detection Technologies manufactures Perimeter Intrusion Detection Systems (PIDS) that detect climbover and breakthrough activity along the perimeter fence or wall Hundreds of sites have been effectively protected by Detection Technologies worldwide Our staff can draw on 100 manyears of in the design of PID solutions. Caution signs danger warning yellow and black tape, poison biohazard striped, high voltage security perimeter elements symbols set safety exclamation, attention electricity zone illustration winwinartlab.
A company came to Wood and wanted a perimeter security system with all the hightech bells and whistles cameras, CCTV, sensors When he went out to the facility to take a look at what the company was already doing in terms of perimeter security, Wood discovered that the fence surrounding the property had fallen down in several locations. Keywords Security lighting, Illumination, Perimeter Area, Cameras Surveillance System 1 INTRODUCTION Security lighting is an important part of the perimeter security plan On most projects, however, little consideration is given to the security design and layout Usually, lights are installed, and that is far as it goes. Perimeter Protection is supported for the following IVS Features Tripwire, Intrusion, Fast Moving This guide will use Tripwire as an example, but the steps will be identical for the other Rule Types to add an Object Filter.
Security lighting is a wellestablished method of deterring theft and vandalism at electrical substations and other highvalue sites While lighting alone won’t stop a determined intruder, a welllit site can discourage those who would hide under the cover of darkness, assist video surveillance operators by improving visual assessment abilities, and provide better visibility for onsite workers. Logic modules integrate seamlessly with Perimeter Protection devices such as laserbased sensors, which can be synced with a building’s security system If a sensor goes into detection, the logic can signal the alarm to notify the proper authorities Logic can also be used with Maglocks and/or keypads BR3X. Find & Download Free Graphic Resources for Perimeter Security 0 Vectors, Stock Photos & PSD files Free for commercial use High Quality Images.
Perimeter protection is the first line in the defense to detect an intruder The most common points equipped with sensing devices for premise perimeter protection are doors, windows, vents, skylights, or any opening to a business or home Since over 80% of all breakins occur through these openings, most alarm systems provide this type of. Brite Strike Camp Perimeter Security System, Survival Signaling System, Complete Emergency System for Hunters, Campers, Hikers, Fishermen, BSTCAPSS 41 out of 5 stars 50 $2999 $ 29 99 FREE Shipping Only 16 left in stock order soon. Ready to use in multiple sizes.
Get directions, reviews and information for Perimeter Protection in Middlesex, NJ Perimeter Protection 7 Lincoln Blvd Middlesex NJ 046 Reviews (732) Website Menu & Reservations Make Reservations Order Online Tickets Tickets See Availability Directions. Tone alerts provide audible alerts for bands received. Software Defined Perimeter (SDP), also called a "Black Cloud", is an approach to computer security which evolved from the work done at the Defense Information Systems Agency (DISA) under the Global Information Grid (GIG) Black Core Network initiative around 07 Softwaredefined perimeter (SDP) framework was developed by the Cloud Security Alliance (CSA) to control access to resources based.
Security Radar When monitoring large, exposed spaces with harsh weather, and where the perimeter environment is too complex for deployment of only video surveillance cameras, security radar is the ideal option Fewer false alarms using digital beamforming technology and intelligent analysis algorithms;. Set Up Perimeter Protection on your device using various interfaces > How To Set Up Perimeter Protection Alarm Configure responses when the Perimeter Protection alarm is triggered, such as email notifications or alarm output Click the icon under Trigger to set any corresponding event triggers Click Apply to save all settings WebUI Old. Perimeter security icons gg GoGraph Stock Photography, Illustrations, and Clip Art allows you to quickly find the right graphic Featuring over 42,000,000 stock photos, vector clip art images, clipart pictures, background graphics and clipart graphic images.
Rim protection is not obsolete More shots were taken at the rim—which NBAcom defines as coming within five feet of the basket—than beyond the arc Teams combined to shoot a total of 4,172. “In general terms, perimeter security is defined as those elements and systems that allow the protection of perimeters in sensitive installations from being attacked or invaded by intruders So. Outline Perimeter Security Icons Simple set of perimeter security related vector icons for your design Note This purchase is a single image file Image Editor Save Comp Similar Illustrations See All Traces on the ground, service shepherd, security camera, fingerprint Prison set collection icons in outline style vector symbol stock.
Perimeter security icons Clipart Fotosearch Enhanced k Fotosearch Stock Photography and Stock Footage helps you find the perfect photo or footage, fast!. We feature 61,000,000 royalty free photos, 343,000 stock footage clips, digital videos, vector clip art images, clipart pictures, background graphics, medical illustrations, and maps. Download 399 environmental protection icon free vectors Choose from over a million free vectors, clipart graphics, vector art images, design templates, and illustrations created by artists worldwide!.
BEA's people counting solutions include a networked sensor designed to count and record the flow of pedestrian traffic in, out and through a building. USM Permanent Guardrail The USM Guardrail system provides permanent fullperimeter fall protection The unique design allows 100% watertight installation under standard roofing and sheet metal details including coping caps, drip edges, gravel stops and even inside most commercial gutters without penetrating the roof membrane. Perimeter Security Icons Simple set of perimeter security related vector icons for your design Note This purchase is a single image file Image Editor Save Comp Similar Illustrations See All Material disign icons security set Door relay, window, glass break, infrared PIR, smoke sensors.
Endpoint users outside of the perimeter need dedicated, multivector phishing protection Boost Network Controls Turn existing network security controls into a realtime defense against phishing threats Abuse Inbox Management Simplify and expedite abuse inbox management and phishing incident response. Security, or more specifically cybersecurity, is at the forefront of everything that RODIN does We believe that the best form of security needs to be integrated across your entire business;. Find & Download Free Graphic Resources for Perimeter Security 0 Vectors, Stock Photos & PSD files Free for commercial use High Quality Images.
The fullarea enclosure around the perimeter of the building enables all work to be carried out in complete safety, protected from all weather conditions A loading platform can be integrated into the protection screen for straightforward, safe repositioning of slab formwork, tools and other materials. IStock Perimeter Security Icons Stock Illustration Download Image Now Download this Perimeter Security Icons vector illustration now And search more of iStock's library of royaltyfree vector art that features Accessibility graphics available for quick and easy download. Coronavirus, covid, infection, protection, termometer, virus icon Open in icon editor This is a premium icon which is suitable for commercial work Use it commercially No attribution required Comes in multiple formats suitable for screen and print;.
This is a Data Protection icon We've made it in iOS style, first introduced in iOS version 7 and supported in all later releases up until now (at least iOS 11)This style is based on thin twopixel lines and is optimized for 50x50 pxUnlike other vector icon packs that have merely hundreds of icons, this icon pack contains 9,752 icons, all in the same style and quality. DaPIS the Data Protection Icon Set In the period March – July 18, we held a series of participatory design workshops with the collaboration of the Academy of Fine Arts of Bologna and the Società Italiana Informatica Giuridica It was a beautiful experience design students, lawyers, computer scientists, communication experts and interested citizens cocreated a consistent set of icons. Detection Technologies manufactures Perimeter Intrusion Detection Systems (PIDS) that detect climbover and breakthrough activity along the perimeter fence or wall Hundreds of sites have been effectively protected by Detection Technologies worldwide Our staff can draw on 100 manyears of in the design of PID solutions.
Find & Download Free Graphic Resources for Perimeter Security 0 Vectors, Stock Photos & PSD files Free for commercial use High Quality Images. Endpoint security remains one of the core data protection principles required with cloud adoption and digital transformation Consider insider threats – Device theft doesn’t necessarily require someone from outside the organization to penetrate your perimeter. Perimeter Security Icons Simple set of perimeter security related vector icons for your design Note This purchase is a single image file Image Editor Save Comp Similar Illustrations See All Material disign icons security set Door relay, window, glass break, infrared PIR, smoke sensors.
Whether it be end user antivirus, network perimeter protection, or data loss preventionStaff enablement & training also shouldn’t be overlooked as a key pillar of your security strategy. Line Home Security Icons Simple Set of Home Security Related Vector Line Icons Contains such Icons as Door Handle, Lock, Cam, CCTV, Remote and more Editable Stroke 48x48 Pixel Perfect perimeter security stock illustrations. Perimeter security icons by Davooda Finish Purchase About the Product Simple set of perimeter security related vector icons for your design Show More Spread the Word and Earn!.
360 degrees of complete perimeter protection, detecting signals from the front, sides, and rear Protection against all radar guns including Xband, Kband, Superwide Kaband, and laser Icon display provides distinct visual symbols of alerts detected and engaged modes;. Perimeter security icons gg GoGraph Stock Photography, Illustrations, and Clip Art allows you to quickly find the right graphic Featuring over 42,000,000 stock photos, vector clip art images, clipart pictures, background graphics and clipart graphic images. Perimeter protection is simply not enough Today’s threats demand technology steeped in intelligence, leadership and policy Last week, I had the opportunity to talk to almost 0 Clevel.
Caution signs danger warning yellow and black tape, poison biohazard striped, high voltage security perimeter elements symbols set safety exclamation, attention electricity zone illustration winwinartlab. We feature 61,000,000 royalty free photos, 343,000 stock footage clips, digital videos, vector clip art images, clipart pictures, background graphics, medical illustrations, and maps. Targets), target perimeter, security perimeter, perimeter security, attacks and threats, and risk are addressed The second section of the report builds from the first and presents several models which, taken together, provide a general conceptual framework for considering the need for, and nature of, standards for perimeter security.
The best selection of Royalty Free Perimeter Vector Art, Graphics and Stock Illustrations Download 1,0 Royalty Free Perimeter Vector Images. Line Home Security Icons Simple Set of Home Security Related Vector Line Icons Contains such Icons as Door Handle, Lock, Cam, CCTV, Remote and more Editable Stroke 48x48 Pixel Perfect perimeter security stock illustrations. The SecurityInfoWatchcom Perimeter Security category is a collection of news, analysis, and other information relevant to security professionals involved in hardening of building and facility.
Set Up Perimeter Protection on your device using various interfaces > How To Set Up Perimeter Protection Alarm Configure responses when the Perimeter Protection alarm is triggered, such as email notifications or alarm output Click the icon under Trigger to set any corresponding event triggers Click Apply to save all settings WebUI Old. Find & Download Free Graphic Resources for Protection Icon 16,000 Vectors, Stock Photos & PSD files Free for commercial use High Quality Images. Physical security controls include such things as data center perimeter fencing, locks, guards, access control cards, biometric access control systems, surveillance cameras, and intrusion detection sensors Digital security controls include such things as usernames and passwords, twofactor authentication, antivirus software, and firewalls.
PERIMETER PROTECTION FIBER OPTIC FENCE IR BEAM SENSOR MICROWAVE SENSORS RADAR BURIED CABLE TAUT WIRE FENCE SEARCH Company About All content on this web site, such as text, graphics, logos, button icons and images is the property of Neural Integrated Systems Pvt Ltd (NISPL), or its content suppliers and protected by international. Earn commission from each customer you refer Join our Partner Program Product Specs Created Mar 19, 17. IStock Perimeter Security Icons Stock Illustration Download Image Now Download this Perimeter Security Icons vector illustration now And search more of iStock's library of royaltyfree vector art that features Accessibility graphics available for quick and easy download.

It Security Protect Your Uk Business From Cyber Threats With Network Roi
Perimeter Security Icons Simple Set Of Perimeter Security Related Vector Icons For Your Design Canstock
Heras Nederland Experts In Perimeter Protection
Perimeter Protection Icon のギャラリー
It Security Open Reality
Guard Key Lock Protection Safety Security Icon Download On Iconfinder
Firewall Perimeter Security Lp Networks It Specialist Lp Networks

Home Forteza Europe

Forteza Jsc Manufacturer Of Perimeter Protection Detectors
Why Identity Is The New Perimeter Check Point Software

Electric Guard Dog Becomes Amarok 02 03 Sdm Magazine
Heras Nederland Experts In Perimeter Protection
Check Drone Fence Guard Patrol Perimeter Security Icon Download On Iconfinder
Senstar Fiberpatrol Fp1150 Fiber Optic Data Conduit Protection

Viamon The Monitoring Company
Q Tbn And9gctlvo9d3g7me9myclzd9iudr Pvzu9tmxqronkr0pazf2piu5ux Usqp Cau
Perimeter Security Icons Simple Set Of Perimeter Security Related Vector Icons For Your Design Canstock
Heras Nederland Experts In Perimeter Protection
Alert Code Guard Protection Security Signaling System Icon Download On Iconfinder
Torsus Intrusion Detection System For Rigid Metal Fences
Lookout Personal For Android

Perimeter Walk Covid 19 Control Measures The Peacelink
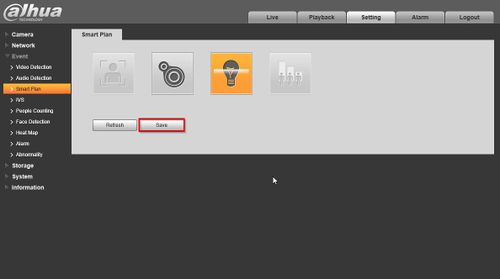
Dahuawiki
Network Security Secops
It Security It Data Network Security Solutions Services Consulting Empowered
Guard Insurance Lock Open Protection Security Unlock Icon Download On Iconfinder

Perimeter Protection Systems Kildare Laois Dublin Ireland

Hse Concept Occupational Safety And Health Danger Perimeter Production Factory And Environment Labor Preventive Instructions Worker Protection Vector Icon Set Stock Illustration Download Image Now Istock
Senstar Transportation Security Airports Rail And Transit Systems Senstar

Security System Installers Perimeter Fence Alarm System
Senstar Starnet Sms Security Management System
Harrisons Fire Security Services Leading Independent Security Providers In The Home Counties Area Of England

Perimeter Protection Companies Ifsec Global Directory

Lookout Personal For Android
What Is Waf
Security Icons Stock Vector Illustration Of Password
Independent Electronic Security Systems Specialists Vistec Systems
Borderless Network Security Certitude Security Cyber Security
ᐈ Security System Icons Stock Vectors Royalty Free Security System Illustrations Download On Depositphotos
Custodial Qsg
Quanergy S 3d Ai Powered Physical Security Solutions

Perimeter Security Network Roi Protecting Your Business Technology

Toggle Create Total Security Protection
Application Data Network Security Layer With Lock Icon In Center Presentation Powerpoint Images Example Of Ppt Presentation Ppt Slide Layouts
Safety And Security Icons Set Stock Vector Illustration Of Pictogram House
What Is Serverless Security Check Point Software
Smart Home Solutions Security Surveillance Residential Commercial Automotive Electronics Springfield Il
The Internet Of Secure Things What Is Really Needed To Secure The Internet Of Things Icon Labs
Sentinel Network Integrity Systems
Boundary Fence House Perimeter Protection Icon Download On Iconfinder

Elko To Distribute Mitech Perimeter Security Solutions
Guard Lock Protection Safety Security Shield Icon Download On Iconfinder
Perimeter Intrusion Detection Navtech Radar
Perimeter Security Equipment Advanced Perimeter Systems
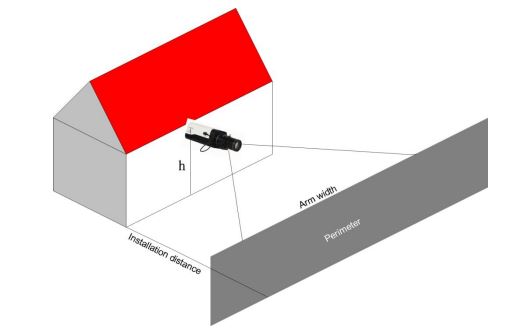
Dahuawiki
ᐈ Security System Icons Stock Vectors Royalty Free Security System Illustrations Download On Depositphotos

Fire Protection Signs Emergency Pictogram Icon Set Vector Clipart K Fotosearch
Smart Home Solutions Security Surveillance Residential Commercial Automotive Electronics Springfield Il
Senstar Correctional Facilities Perimeter Security And Personal Duress Senstar
Cyber Security Consultancy Services Cyber Risk Advisory
Network Security Icons Fortinet
Global Acs Perimeter Security
Detector Door Guard Handle Security Sensor Icon Download On Iconfinder
Home Perimeter Security Group
Network Security Icons Fortinet
Building Guard Home House Lock Protection Security Icon Download On Iconfinder
Security Icons Royalty Free Cliparts Vectors And Stock Illustration Image

Affordable Radar Solutions Security Applications Magos Systems
High Security Fencing Perimeter Security Fences Zaun Fencing

Check Point Security Appliances Security Gateways Checkfirewalls Com
Heras Nederland Experts In Perimeter Protection
Advanceguard Navtech Radar

Home Perimeter Security Group
What Is Waf
24 Hour Perimeter Protection Security Industry Association
Cybersecurity Consulting Services Fortinet
Perimeter Security Icons Stock Vector C Davooda
Perimeter Security Icons Simple Set Of Perimeter Security Related Vector Icons For Your Design Canstock
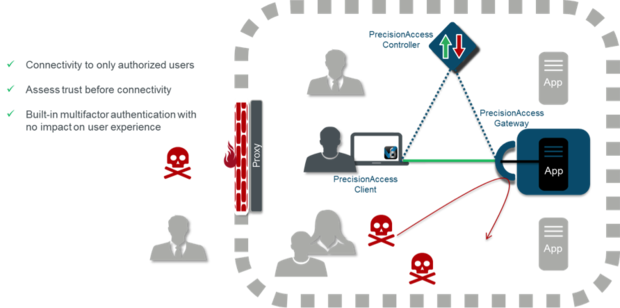
Vidder S Software Defined Perimeter Puts Tight Security Around High Value Assets Network World
Perimeter Safety Danger Protection Secure Security Icon Download On Iconfinder
Security Building Technology Siemens Global
All Weather And Light Conditions Navtech Radar
Senstar Starnet Sms Security Management System
Network Security Secops
High Security Fencing Perimeter Security Fences Zaun Fencing
Security Bollards Hormann Uk
Fortinet Enterprise Security Without Compromise
Lookout Personal For Android
Outdoor Perimeter Protection Outdoor Icon Png Black Transparent Cartoon Jing Fm
Senstar Intelligent Lighting Security System
Home Security Vector Icons Set Royalty Free Cliparts Vectors And Stock Illustration Image
Perimeter Intrusion Detection
Deep Wall The Definitive Solutionfor Perimeter Protection
High Security Fencing Perimeter Security Fences Zaun Fencing

Perimeter Protection Home Solutions Home Securtiy Company

Home Perimeter Security Group
Data Classification The Foundation Of Your Data Security Solution Titus

Security System Installers Perimeter Fence Alarm System
Perimeter Security Icons Stock Vector Illustration Of Care
High Security Perimeter Specialist Nz Hampden Hampden
What Is Endpoint Protection Check Point Software
Unique Quality Made In Germany




